Matchless Info About How To Detect Confiker C

This just came in:
How to detect confiker c. Please download malwarebytes to your desktop. Conficker.a infections cannot be detected this way. Microsoft analyst joshua phillips gives an alternative interpretation of the name, describing it as a rearrangement of portions of the domain name trafficconverter.biz (with the letter k, not found in the domain name, added as in trafficker, to avoid a soft c sound) which was used by early versions of conficker to download updates.
Leder and tillmann have also. Brief overview of the conficker worm and how the languardian can be used to detect its presence checks if a host is infected with conficker.c or higher, based on conficker's. Malwarebytes can detect and remove worm.conficker without further user interaction.
Conficker e is released aimed at infecting computers infected with conficker c. Download conficker worm fix note: How to check / find and remove conficker worm.
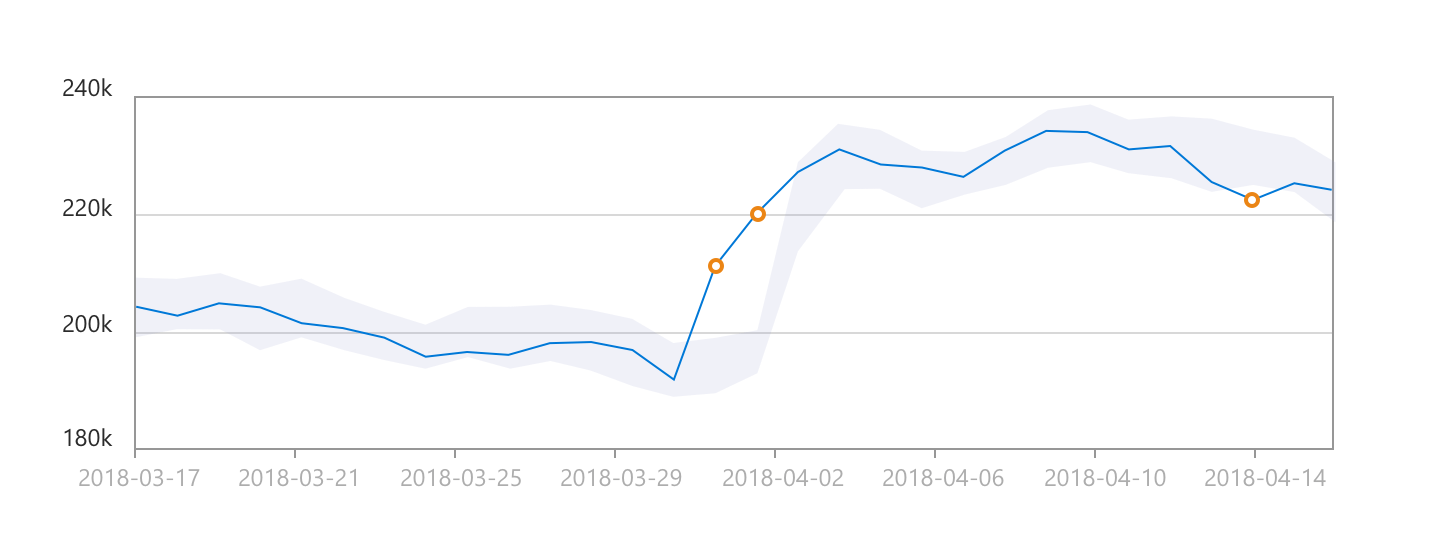
There is lot of buzz going around for conficker worm aka downadup which targets the microsoft windows operating system. A quick visual scan can tell you whether you're infected with the conficker worm or similar malware. Pcs infected with the third version of the worm, conficker.c, are scheduled to phone home and receive their updates on april.
Use the following free microsoft software to detect and remove this threat: When conficker.c or higher infects a system, it opens four ports: 6 answers sorted by:
The new conficker tools are timely: Overview this article explains how to track and find conficker infections on your network. The plugin now uses credentials, if available, and.
You can scan a network to detect confiker infections due to the way confiker patched the vulnerability. The origin of the name conficker is thought to be a combination of the english term configure and the german pejorative term ficker (engl. Please click on the start button to have the program scan your computer and remove any downadup and conficker infections on your computer.
Microsoft defender antivirus for windows 10 and windows 8.1, or microsoft security. Click below to check your system (for. Tenable has released version 2.0 of the conficker plugin (plugin id 36036), which includes the following updates:
Detecting conficker in your network authors: First and foremost, there is not reason to panic. The conficker working group uses namings of a, b, b++, c, and e for the same version respectively.
The conficker worm copies itself on the accessible usb drives. Conficker, as of this writing, is nearly eight years old, and almost every antivirus available today can detect and quarantine the worm before it spreads. 5 the latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445 services on infected machines.